YARA
Overview
YARA is an open-source tool designed to help malware researchers identify and classify malware samples. It makes it possible to create signatures for malware families based on textual and/or binary patterns.
YARA support in Sublime enables you to better block known malware using open-source YARA signatures, your own custom YARA signatures, and YARA signatures shared by your peers.
With YARA + MQL, you can combine your YARA signatures with powerful email context like first-time sender or Azure AD Group recipients to block malicious files before they're detonated. You can also use YARA signatures to Hunt over historically received files via email.
Getting started
In order to use YARA signatures in your Sublime rules, you must first add a Feed that points to a private or public Git repository containing the signatures you wish you use.
After adding the Feed, the YARA signatures will be ingested automatically, and will run each time you invoke MQL's file.explode() on both the original file passed to the function as well as every file that is recursively extracted.
Creating a Feed
- First, identify or create a Git repo containing the YARA signatures you want to use. If you don't have one yet, you can either:
a. follow our testing instructions to see YARA working end to end
b. or use one of the public YARA repos we've linked below - Within the
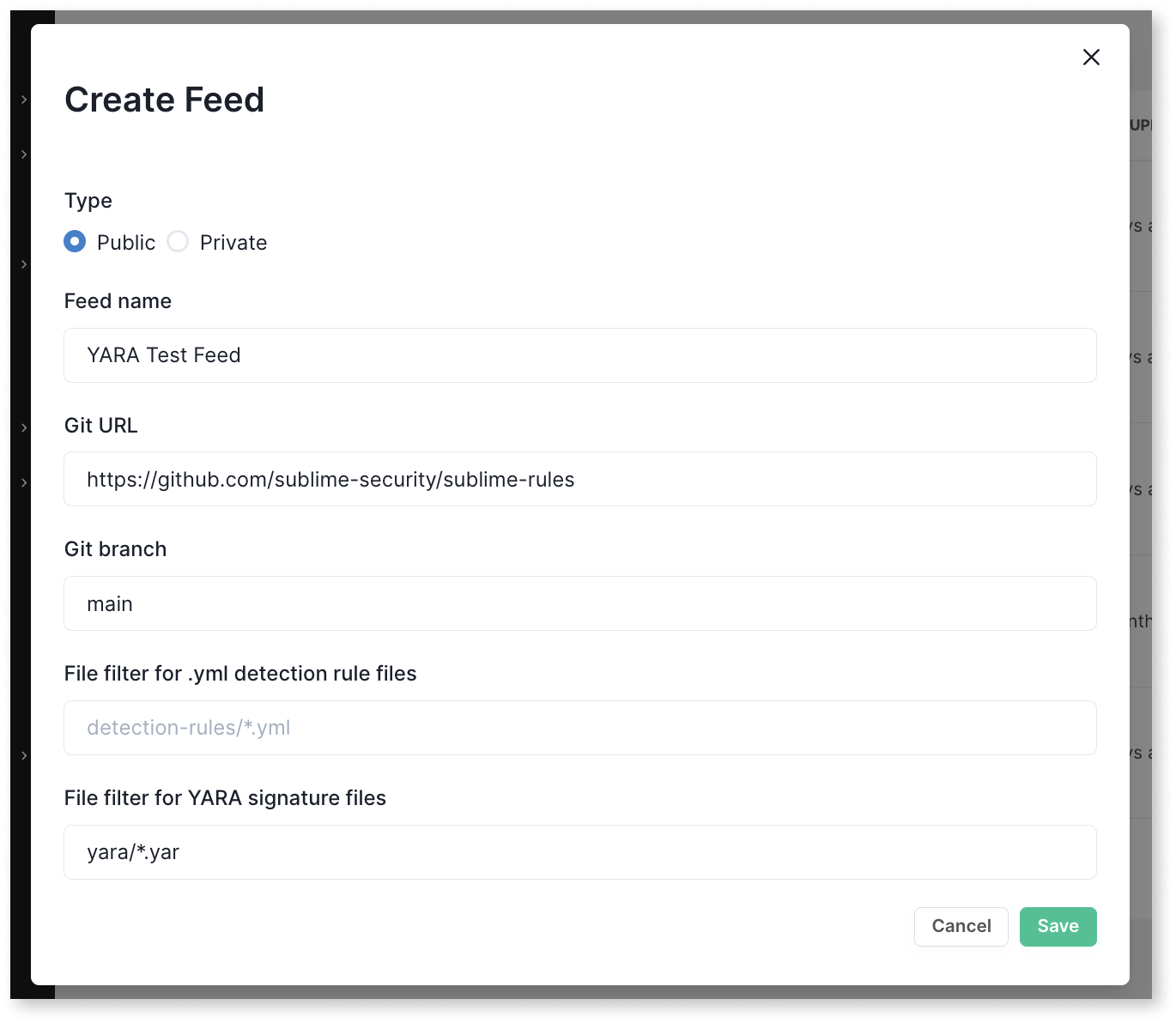
Feedssection of your Dashboard, clickNew feedin the top right-side corner. - Name the Feed, for example:
My YARA signatures - Enter the URL for any private or public Git repository consisting of one or more YARA signatures.
- Enter the respective Git branch.
- Enter the glob pattern for where the YARA signatures are within the repo. For example, if they’re in the root level yara/ directory, enter
yara/*.yar. - Click
Save.
YARA signatures will be compiled and validated on Feed creation. The Feed will surface the number of YARA signatures ingested into the platform from the repository. If any files fail validation, they will be excluded from the Feed. Errors will appear in the Admin section under System Errors.
⚠️ To look at each YARA signature, you’ll need to view them in the source repository. Viewing YARA signature source within the Sublime Dashboard is currently not supported.
Creating an MQL Rule
Once YARA signatures are ingested via your Feed, they will run by default any time file.explode() is invoked. Any matches will be available in the .scan.yara.matches array of the FileExplode output.
Since FileExplode runs over any file, this means you can run YARA over any attachment or even files auto-downloaded from links via LinkAnalysis.
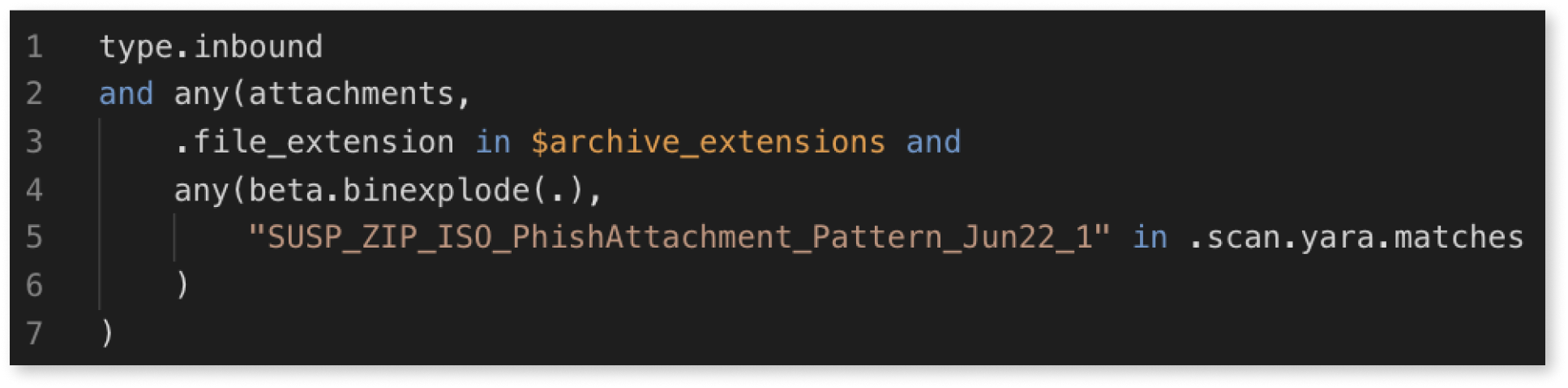
Using FileExplode's .scan.yara.matches, you can look for:
- Any YARA signature match with an archive attachment using the length of the scan matches:
any(attachments,
.file_extension in $file_extensions_common_archives and
any(file.explode(.), length(.scan.yara.matches) > 0)
)
- Specific YARA signature matches using
.name:
any(attachments,
.file_extension in $file_extensions_common_archives and
any(file.explode(.),
any(.scan.yara.matches, .name == "YARA_SIGNATURE_NAME_HERE")
)
)
- Arbitrary YARA metadata matches using
.meta:
Any match from a specific author:
any(attachments,
.file_extension in $file_extensions_common_archives and
any(file.explode(.),
any(.scan.yara.matches, .meta['author'] == "YARA_META_AUTHOR_HERE")
)
)
Any match with a specific severity:
any(attachments,
.file_extension in $file_extensions_common_archives and
any(file.explode(.),
any(.scan.yara.matches, .meta['severity'] == "YARA_META_SEVERITY_HERE")
)
)
When MQL rules flag, the specific YARA signatures that match will be visible in the Investigation page as a new Insight. In the future, we’ll make these visible in the Triage page as well.
Testing YARA in Sublime
If you would like to test out YARA in your Sublime deployment, we’ve added a YARA test rule to our public Git repo. Enter the following details:
- Create a new Feed using the following fields:
- Feed name:
YARA Test Feed - Git url:
https://github.com/sublime-security/sublime-rules - Git branch:
main - Leave MQL file filter blank
- YARA file filter:
yara/*.yar
- Feed name:
- Next, navigate to
Detectionin your left nav and selectCreate- Replace the stub rule with this MQL:
type.inbound and any(attachments, .file_extension in $file_extensions_common_archives and any(file.explode(.), any(.scan.yara.matches, .name == "SublimeStandardTestString") ) ) - Select
Create Rulein the top right- Activate immediately:
On - Name:
YARA: Test Rule - Type:
Detection - Other fields: optional
- Activate immediately:
- Replace the stub rule with this MQL:
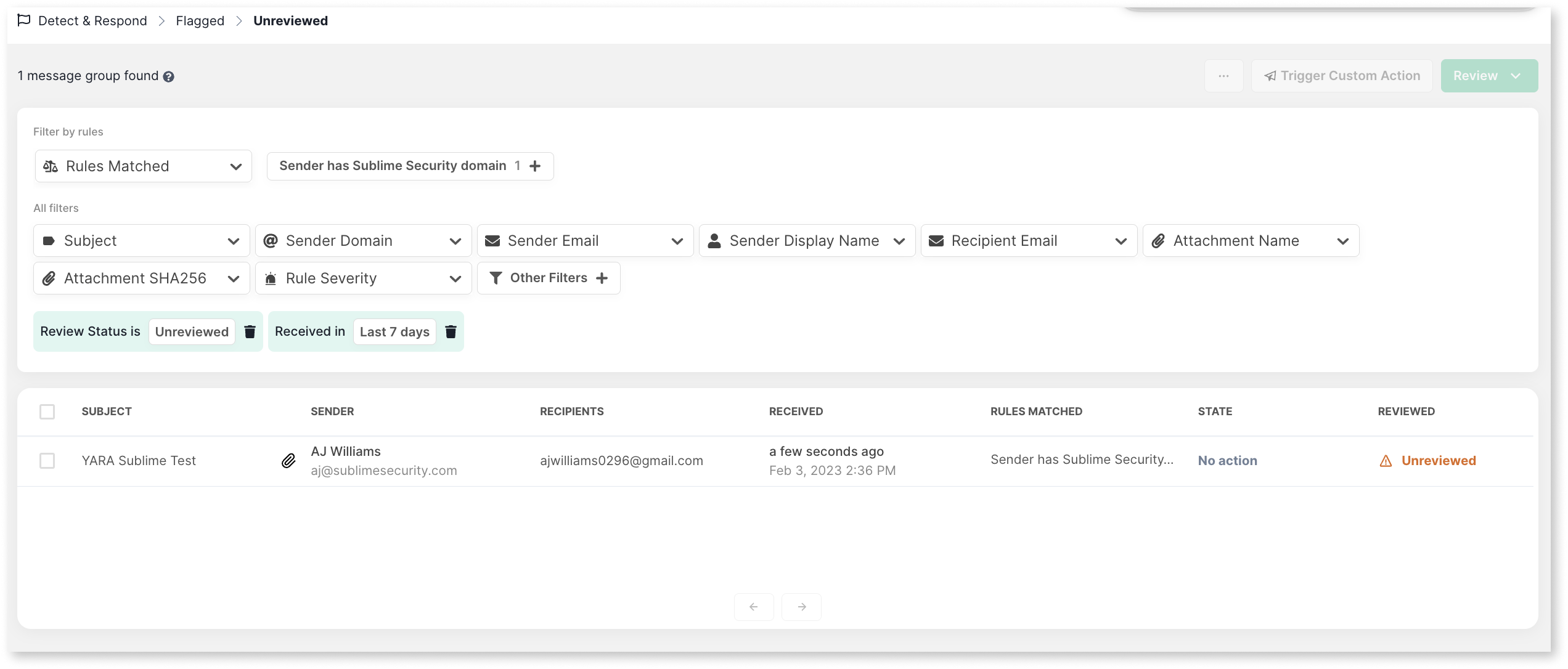
- Download our benign test attachment
(A zip file containing atest.txtfile with the stringSublime-Standard-Test-String) - Send the zipped content from an unmonitored mailbox (e.g. your personal mailbox) to a monitored mailbox (e.g. your work mailbox). Note that if you send the message from a monitored Sublime mailbox, the message type will be
type.internal, nottype.inbound, and the rule will not flag. - You should see the message flagged in your Sublime Dashboard! 🎉
Updated about 1 year ago