Attack Score
Overview
Sublime’s Attack Score is a machine learning-based feature that helps security teams understand and prioritize potential threats based on observed attack indicators in an email message.
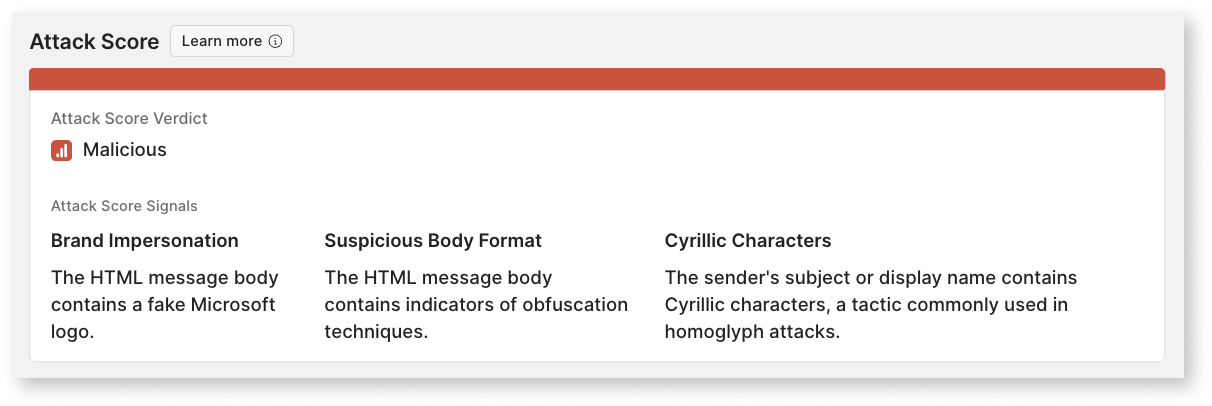
Attack Score is surfaced through a verdict — malicious, suspicious, unknown, or likely_benign — along with corresponding signals to provide easily digestible context during the alert investigation process about the message and the underlying machine-learning model logic.
Attack Score utilizes hundreds of signals written in MQL extracted from various parts of a message, organizational context, past behavior, and more:
-
Headers
-
Attachment metadata
-
Link analysis
-
Sender behavior
-
Content understanding
-
Authentication checks
These signals are analyzed to identify common attack patterns and unusual activity. They are derived from attachments, headers, authentication, message body, links, and sender while leveraging enrichment capabilities such as:
-
Sender behavior profiles
-
Natural Language Understanding
-
Computer Vision
-
WHOIS
-
Domain reputation
-
Attachment analysis
Every Attack Score has 3 components:
- Verdict: This is a description —
malicious,suspicious,unknown, orlikely_benign— utilized to communicate the likelihood of a given message being an attack.Maliciousverdicts signal a threat with strong confidence.Suspiciousverdicts contain patterns indicative of potential threats but are inconclusive.Unknownverdicts are similar to Suspicious as they contain patterns indicative of potential threats but may also contain common benign behaviors.Likely Benignverdicts contain patterns commonly associated with benign email.
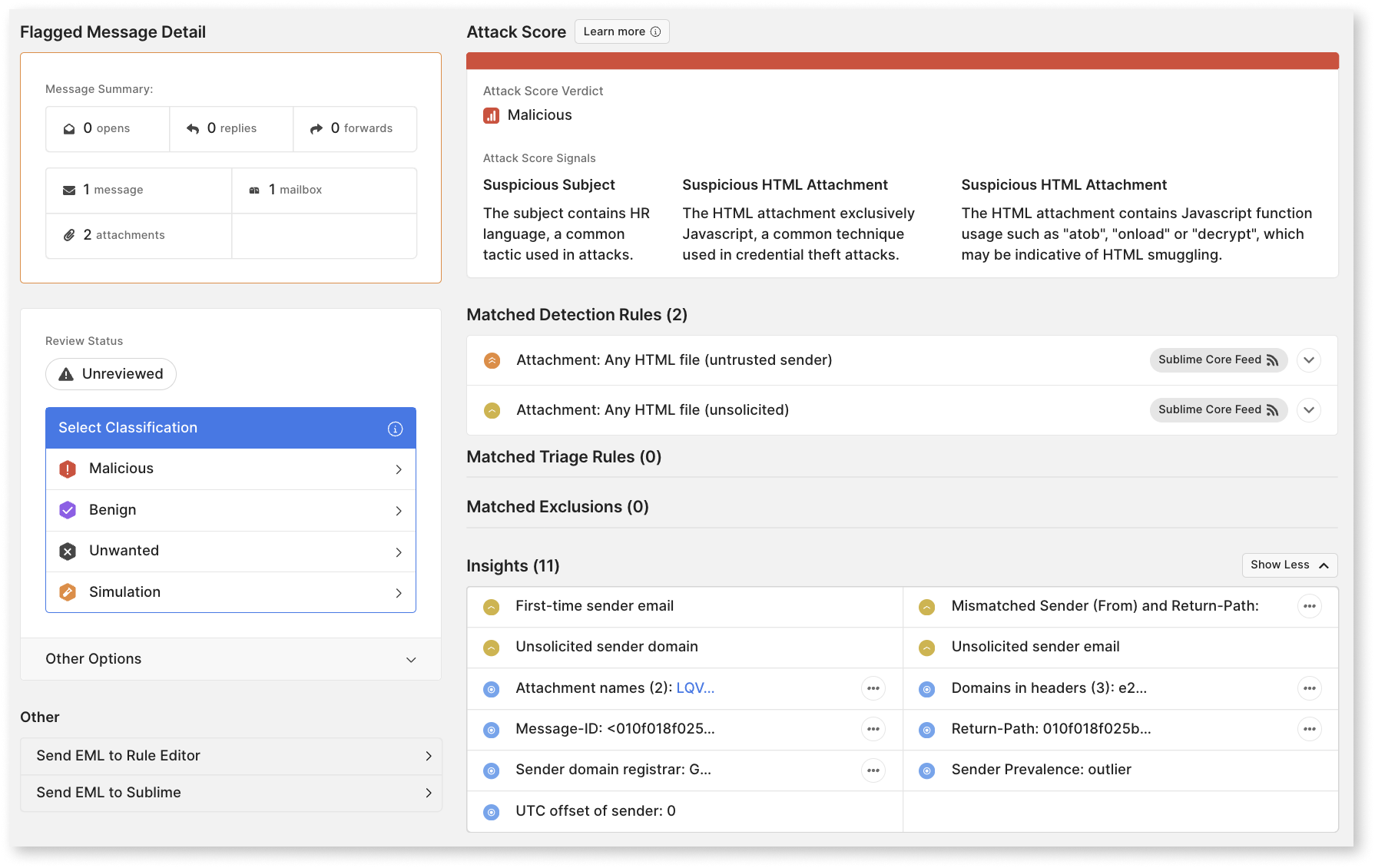
- Top Signals: These are the top 2-5 characteristics that most contribute to a given raw score and verdict, providing context and transparency through explainable ML.
- Raw Score: This is a number from 0-100 that is calculated from the ML algorithm. The raw score of a message determines which verdict is selected. Raw scores are not available in the platform at this time, but are available via the API.
Common workflows
Attack Score can be used in a variety of ways, including:
Auto-remediate high-confidence threats
Sublime's default Attack Score Triage Rule looks for flagged and user reported messages with the malicious verdict. Activate this Rule in your instance and assign auto-quarantine to automatically tackle high-confidence attacks!
In-platform message reviews
You can leverage the Attack Score on any investigation by simply opening the message details within the platform. You do not need to view the message contents in order to view a message’s Attack Score verdict and top signals.
Malicious verdicts are assigned with precision, making them high-confidence indicators of phish and spam in user mailboxes. In general, analysts should spend limited time reviewing these messages, opting instead to classify the message as malicious and move it to quarantine (automatically with Triage Rules or manually with their review).
Suspicious and unknown verdicts are very similar because they both contain patterns indicative of potential threats, but suspicious verdicts indicate a higher likelihood of a malicious message.
Submitting feedback for future ML models
All users are encouraged to share feedback with Sublime about the performance of Attack Score in their environment.
If you would like to provide us with feedback on any of the verdicts or signals provided, please share the EML with our team using the “Share with Sublime” checkbox during the message review or the “Send EML to Sublime” button on the lower left side of the message investigation page. Comments highlighting the details of your Attack Score feedback are welcome!
Enterprise customers can also share specific callouts with the Sublime team through the usual support channels.
“Auto-reviewing” in SOARs
If you utilize a SOAR, you can call our Attack Score API endpoint, /v0/messages/:id/attack_score, in order to enrich your automation.
When the verdict is set to malicious, you can complete your review without manual analyst review by calling the v0/message-groups/review API endpoint to eliminate time spent investigating high-confidence threats.
Support for additional workflows, such as MQL Rules and message triage views, is coming soon!
Updated 24 days ago