Attack Surface Reduction
Attack Surface Reduction, or ASR, is all about mitigating the ways an attacker can conduct a successful attack. On endpoints, app allowlisting leaves attackers with fewer ways to perform attacks. On networks, Secure Web Gateways can block outbound requests to new domains. Now, you can do the same in Microsoft 365 & Google Workspace using Sublime.
If a certain behavior is not normal for your environment, you can block it by default and make exceptions when necessary for legitimate behavior.
Here's a sample ASR Rule to detect inbound messages from newly registered sender domains that you’ve never spoken to before:
type.inbound
and beta.whois(sender․email.domain).days_old < 30
and not profile․by_sender().solicited
When an ASR Rule flags, you’ll see an alert in a view called "Attack Surface Reduction."
Similar to Detection and Triage Rules, you can run this in alert-only mode or configure actions to run: Quarantine, Trash, Warning Banner, Webhook, Slack Alert, etc.
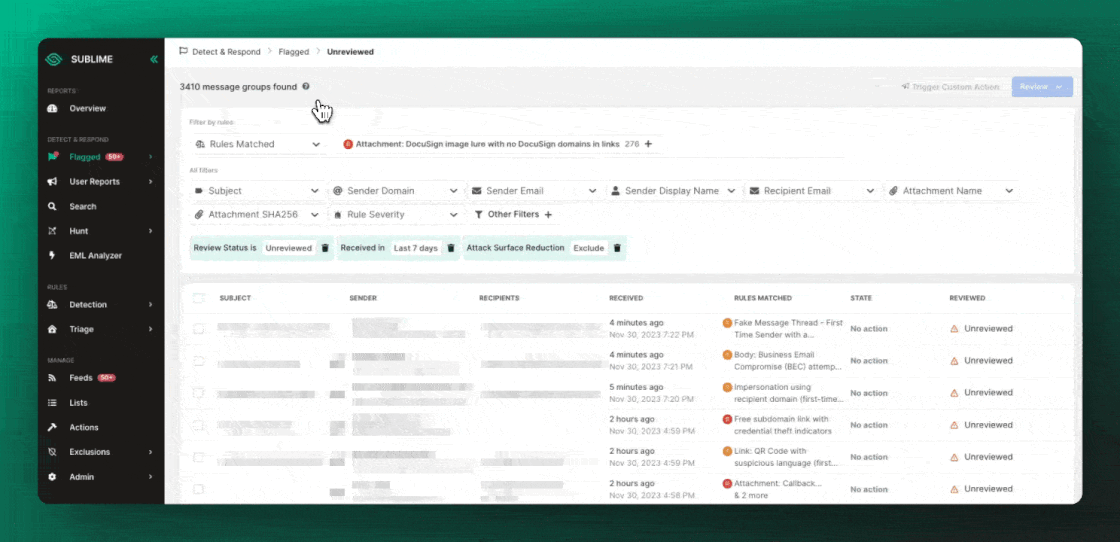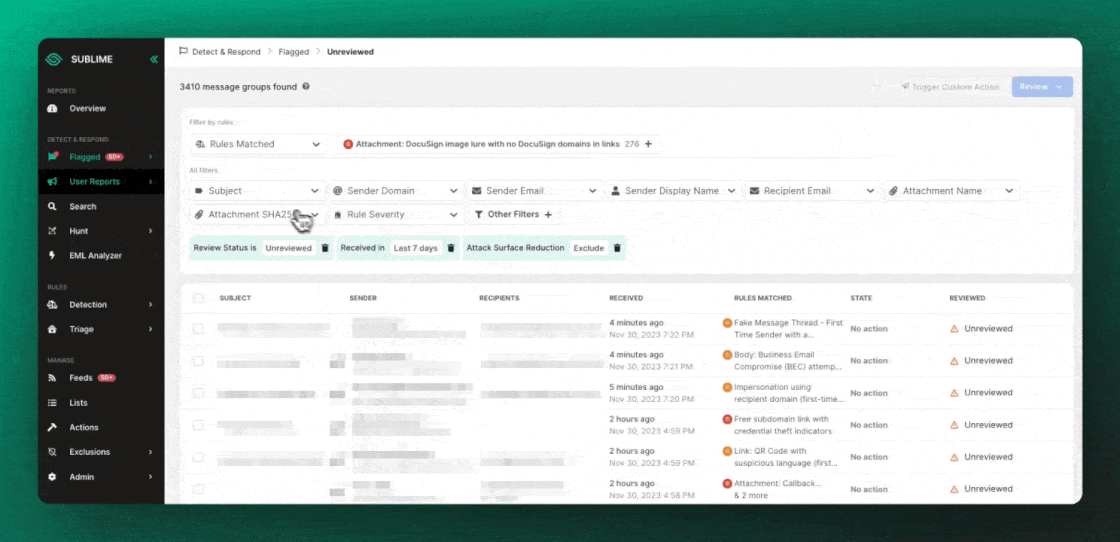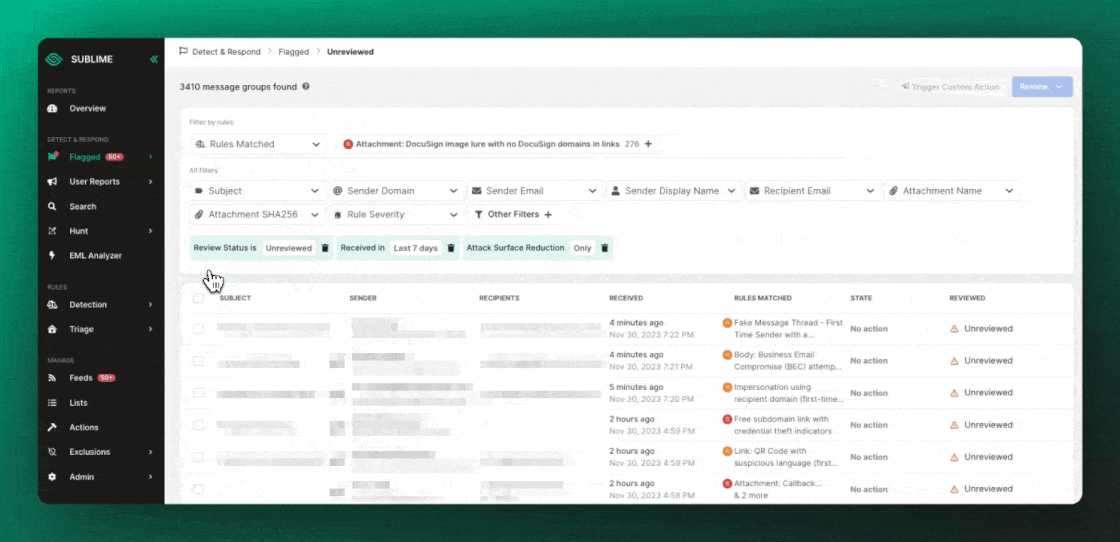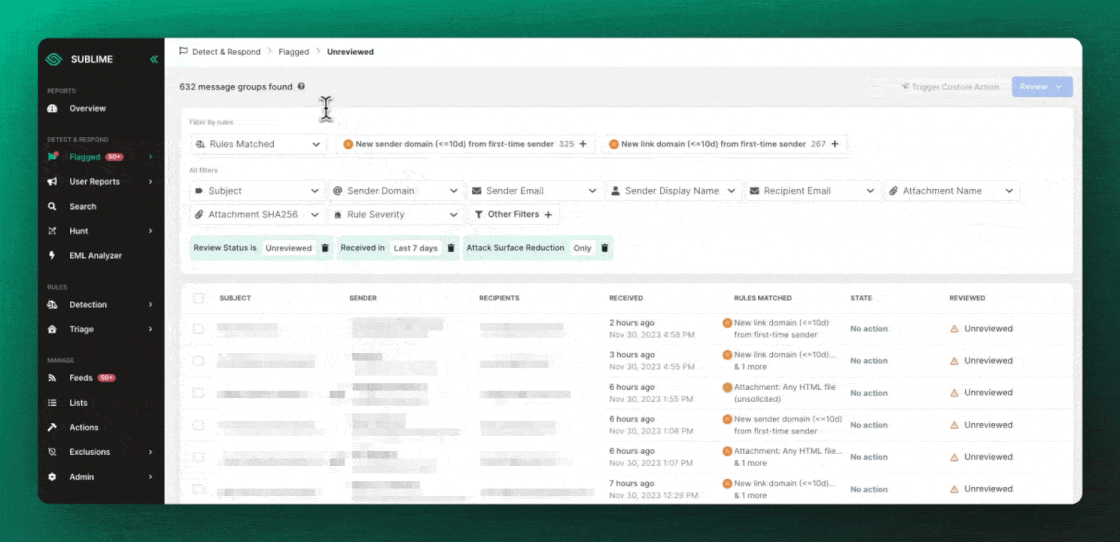
To create your own ASR Rules, simply add the Attack surface reduction Tag to your Rule.
Check out these Core Feed Rules for more examples.
Updated 5 months ago